Digital Twins: Balancing Access and Security
PLM offers clues to managing the competing demands of digital twin users.

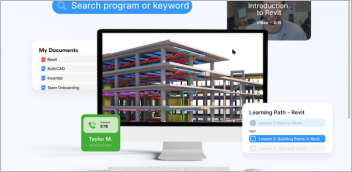
Ansys offers hybrid digital twin solutions that combine data science and simulation. Image courtesy of Ansys.
Latest News
April 2, 2024
As digital replicas of real-world systems and products, digital twins inherited a dilemma from their product lifecycle management (PLM) predecessors. Just like PLM systems, digital twins are at the same time collaboration hubs but also security exposures. For this article, we spoke to digital twin champions and advocates to see how they could address the two seemingly conflicting demands.
Digital Twin’s Priority
“Digital twins today emphasize enabling collaboration more than security,” says Stan Przybylinski, vice president of the analyst firm CIMdata. “While acknowledging digital twins might embody potential security vulnerabilities,” he points out, “PLM implementations in general have to be concerned that only people with the right privileges can access certain types of data. Those data governance practices need to extend to digital twins.”
PTC’s State of Digital Twin 2022 notes, “Twenty-five percent of respondents listed establishing data governance, security and other policies as the primary challenge. Data that is accessible to all is just as dangerous as it sounds, so digital twin developers will likely want to employ secure design philosophies like the principle of least privilege to ensure only authorized users can get at the data.”
Experts add that it’s important to examine the digital twins’ evolving purposes over the product’s lifetime. “Customers are more willing to compromise on security during early investigations when building out and testing digital twins in sandbox environments. As the digital twin approaches production release, security concerns become more important,” says Sameer Kher, senior director of R&D for digital twins at Ansys.
Kher’s observations closely mirror those of Keshav Sundaresh, global director of product management, digital twin and digital thread at Altair.
“If used in sensitive operational decisions, security is the priority,” Sundaresh says. “If used in rapid design iteration, collaboration is the priority.”
The industry verticals also may have different treatments of these competing needs. “Certain industries are innately more stringent due to sensitive data involved,” Sundaresh explains, mentioning examples such as finance, healthcare, and defense.
“There are other industries that prioritize agile innovation whilst keeping security as a priority,” he adds. “They might favor a little bit more collaboration.”
Legitimate or Trivial Concerns
In immersive, interactive digital twin platforms such as NVIDIA Omniverse, the real-world products are represented in lightweight mesh models to enable visualization on mobile devices and augmented reality/virtual reality (AR/VR) hardware. Omniverse uses OpenUSD format, originally developed by the animation studio Pixar, as the visual standard. Unlike CAD models with rich parametric history and dimensions, such mesh models are not sufficiently detailed or precise for manufacturing; therefore, someone stealing the design (topology) from a digital twin to reverse engineer a critical part is less of a concern.
However, because digital twins are inseparably linked to the real-world products, those with malicious intent could remotely trigger destructive events through the digital twins. Also, because they include historical data, they could reveal insights about the products and systems they depict.
“The value of a digital twin hinges on its ability to assimilate data from the physical asset to reflect the real-time behavior or state,” Altair’s Sundaresh says. “This necessitates frequent data updates and collaboration between different functions to ensure effectiveness and consistency.”
The other side of this necessity is the security risk. Sundaresh adds, “The connected nature of the digital twin ecosystem can be vulnerable, since hackers could potentially tap into the system and steal sensitive data. When deployed in white-box form, digital twins can potentially allow competitors to learn more about your design, performance and operational processes.”
Kher speaks to the basis for any concerns. “Concerns usually stem from the fact that the end user of the digital twin is often not the creator. An example would be an operator of equipment such as a furnace wanting to use a digital twin created by the manufacturer … Additional concerns relate to security and vulnerability of the software used in digital twins.”
As for preventive measures, Kher explains, “In most cases, efficient digital twins are deployed as compiled code, making them quite safe from an IP [intellectual property] theft perspective. Encryption and obfuscation allow for additional levels of safeguards for any metadata that may need to be stored with the twin. Authenticated APIs [application programming interfaces] are then the only way to query and access any exposed digital twin interfaces.”
“The bigger risk comes when digital twins might be exchanged with or are exposed to value-chain partners, but overall, we are not at that level of market and technology maturity,” Przybylinski says.
Przybylinski and his CIMdata colleagues are currently conducting a survey on digital twins, targeting software and service providers and industrial users. By the time this article goes online, the survey results will likely be available.
Growing Adoption
Altair’s showed that among the respondents, “Sixty-nine percent (1,393) said their organization currently leverages digital twin technology, while 23 percent (460) said their organization did not. Only 8 percent (154) said they weren’t sure.”
Furthermore, “Forty-three percent of respondents thought that digital twin solutions will make the need for physical testing obsolete within the next four years or sooner.”
“Many functional areas benefit from using digital twins from systems engineers, designers [and] operators to maintenance technicians,” Sundaresh says. “Flexible access control for shared access across these functions is key.”
More Altair Coverage
More CIMdata Coverage
More PTC Coverage
Subscribe to our FREE magazine, FREE email newsletters or both!
Latest News
About the Author
Kenneth Wong is Digital Engineering’s resident blogger and senior editor. Email him at kennethwong@digitaleng.news or share your thoughts on this article at digitaleng.news/facebook.
Follow DE